About this paper
Inside Certificate Chains Beyond Public Issuers:Structure and Usage Analysis from a Campus Network
Hongying Dong, Yizhe Zhang, Hyeonmin Lee, and Yixin Sun University of Virginia
This paper has been published at IMC 2025.
Summary
We conduct research on the large-scale study of TLS certificate chains issued by non-public issuers (those absent from major browser root stores and the CCADB). Using one year of campus network traffic comprising over 259.3 million TLS connections and 731,175 certificate chains, we analyze how these certificate chains are structured and used in real-world deployments. Our findings reveal that unnecessary certificates frequently appear in these chains, leading to inconsistent validation outcomes across clients. We also observe a shift toward automated certificate management, with many servers transitioning to Let’s Encrypt over time. The study underscores the need for better tooling and automation to ensure consistent, interoperable, and secure TLS deployments.
Key findings
- Certificate chain categorization & chain length distribution: We provide a classification of certificate chains based on our large-scale analysis:
- Public-DB-only: Certificate chains that exclusively comprise certificates issued by public-DB issuers—i.e., issuers listed in at least one major Web PKI root store (Apple, Microsoft, Mozilla) or in the CCADB.
- Non-public-DB-only: Certificate chains that exclusively comprise certificates issued by non-public-DB issuers—i.e., issuers whose certificates are not present in any public root store or CCADB, including self-signed certificates. This category excludes chains associated with TLS interception cases.
- Hybrid: Certificate chains that include certificates issued by both public-DB and non-public-DB issuers. These chains are analyzed separately due to their mixed structure.
- TLS interception: Certificate chains containing certificates issued by entities identified as performing TLS interception (e.g., corporate firewalls or security appliances).
Figure: Distribution of certificate chain length.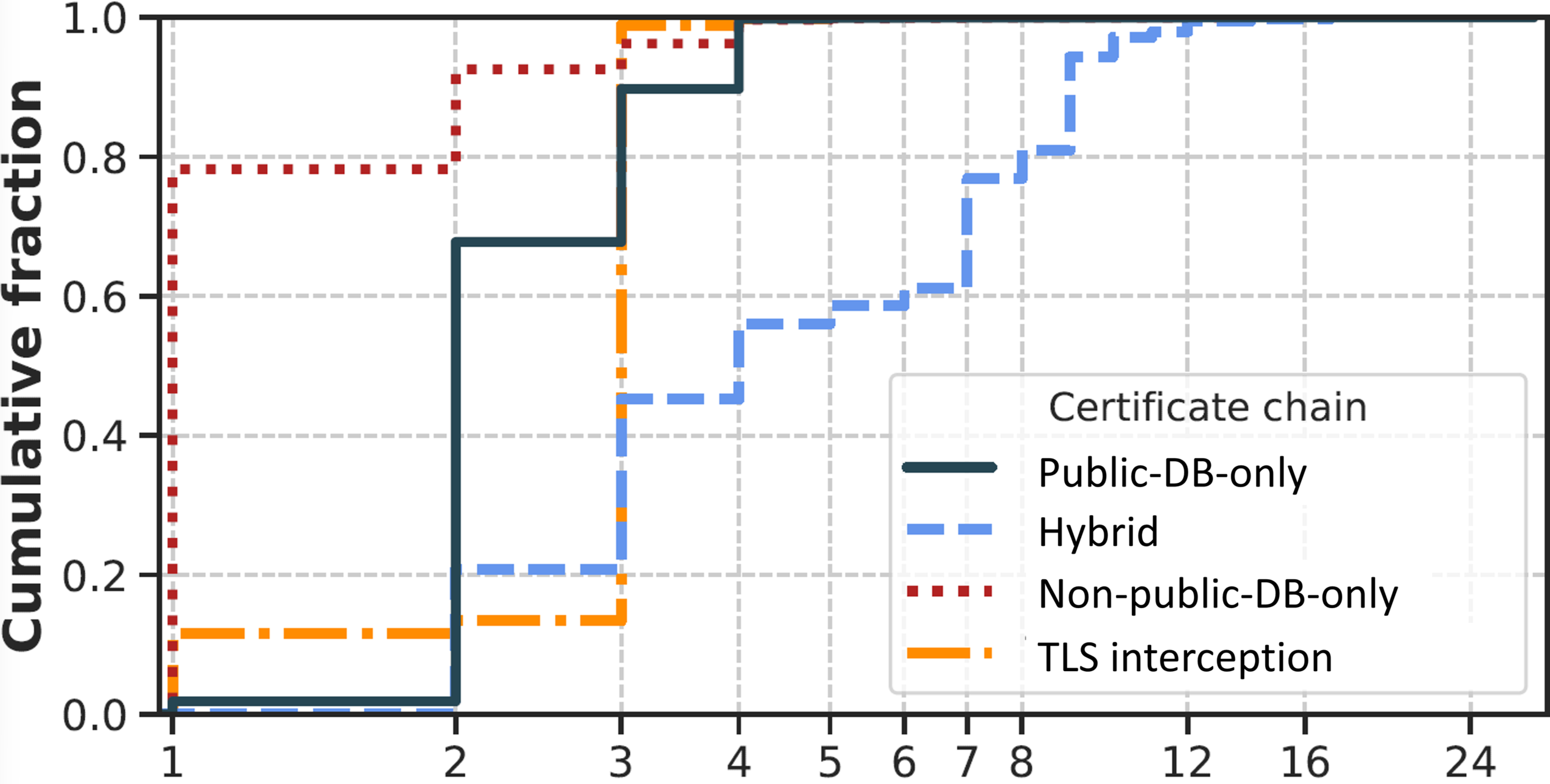
-
Unnecessary certificates: Many certificate chains delivered by servers, even when anchored to a public trust root, include unnecessary certificates that do not contribute to the chain of trust. Such redundant certificates can lead to inconsistent validation results across applications: browsers like Chrome often succeed using maintained trust stores, while validation mechanisms relying solely on the presented chain may fail.
-
Shift towards Let’s Encrypt: In our retrospective measurement (Section 5 of the paper), we found that about 60% of tested domains have transitioned from chaining leaf certificates issued by non-public-DB issuers to public trust roots, to using public issuers such as Let’s Encrypt. This reflects a shift toward automated, user-friendly certificate management, reducing misconfigurations and validation failures.